Sherlogs
Simplicity is the key…
It is a simple bash script that seeks to do the task of viewing the logs of a centos server in an easy way, there are many tools to do the same but the idea of this is to serve as a guide for other distros.
This script does not use dependencies or anything from third parties, its use is relatively easy and its adaptability is very easy. It can become an excellent weapon for the good administration and monitoring of the systems.
Demo
Case 1
Suppose we have an http service running and suddenly the service is down or slower than it should normally run, to find out what happens we must check the logs to see what happens but with sherlogs we can do it faster.

Utility performance
La primera condicion es que seamos root sino pasaria esto con el script:
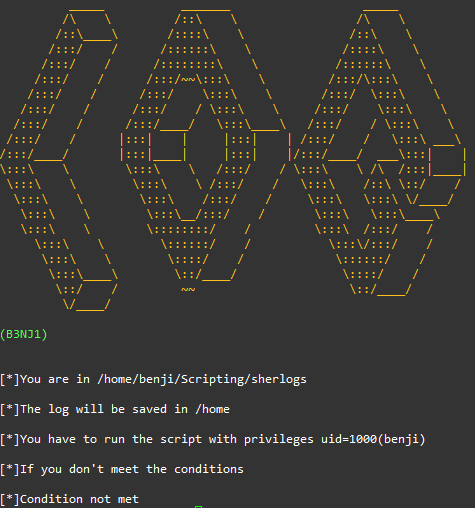

The first condition is that we must be root, otherwise this will happen with the script:
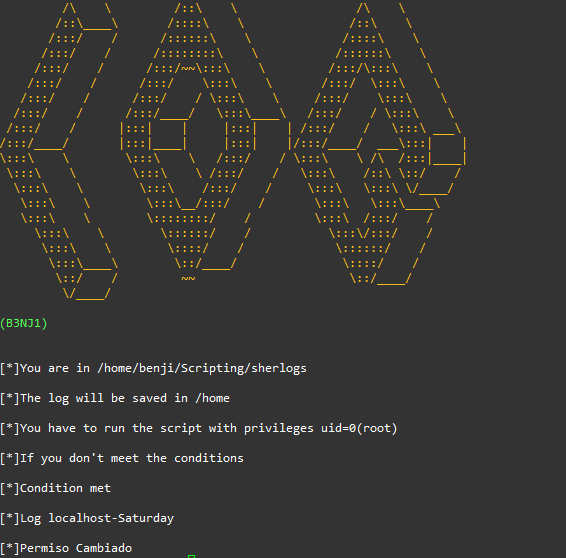

I’m running it in a lab but it can also be done in a real way because the script filters the logs to not extract them all, you can modify the amount of lines you want it to extract.
As the script is executed by root for the other users it would not be visible so what I have done is to change the permissions of the tablet.


Read logs
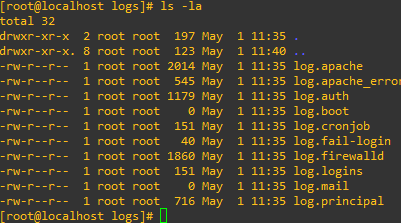

The idea would be that we have a way to see all the logs grouped together. It should be noted that the script is a guide so you can adapt and edit this script as you see fit.
Case 2
Let’s suppose that our server can be configured from ssh, the idea would be to know which ip addresses can connect and which have failed to block the ip or take other measures.
For this case I will create a user and assign a not so robust passwd to it
jusepe
password1

Everything ready, we start with case 2:
The idea is that two friend will try to enter the server but I have not given him the pass nor the ssh user, then he will use what is known as brute force against my server, I will wait a while for him to try everything and I will show the result.
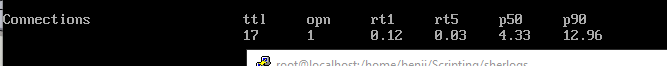

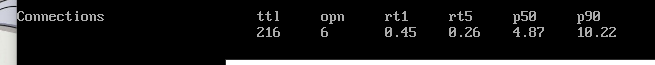

Here I have adapted the script to widen the display spectrum:

After several minutes he was able to enter the server with a brute force attack:
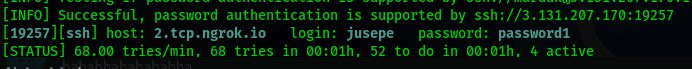


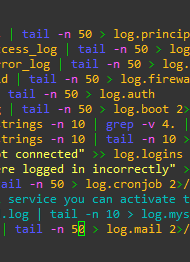
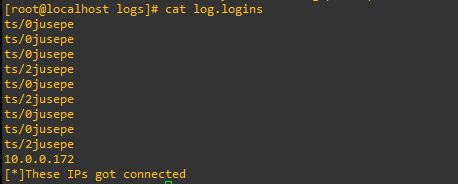
Now we are going to read the logs. Here we can see how the user jusepe logged in several times to the computer, this raises suspicions

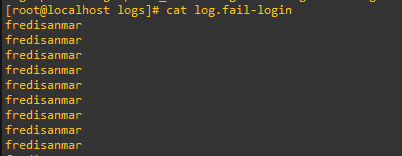
Now we see how it tried to log in with an invalid user, then we can conclude that we are doing a brute force attack.

Recommendation
-
The recommendation is to block the account after recurring failed attempts
-
Another one is to disable the root user through SSH, although in this case it was not seen.
## Conclusion
This is a simple utility that can be of help in different cases.
*This utility was only tested on centOS 8.